Microsoft Entra
Configure Microsoft Entra¶
This guide covers how to configure Microsoft Entra as an identity provider for OpenFaaS IAM.
-
Sign in to Microsoft Entra admin center
-
Create a new Application for OpenFaaS
Browse to Identity -> Applications -> Enterprise applications -> All Applications. In the All applications pane, select New Application.
This will let you browse the Microsoft Entra Gallery. Select Create your own application.
Fill out the app name, select the option
Register an application to integrate with Microsoft Entra ID (App you're developing)and click Create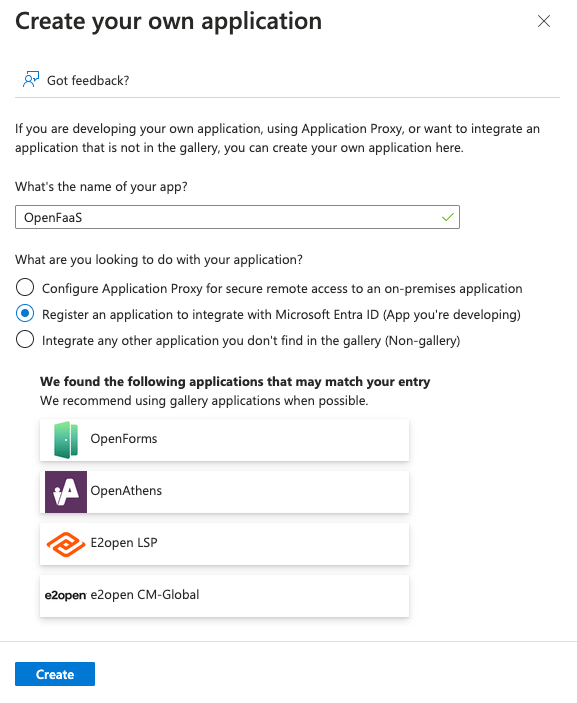
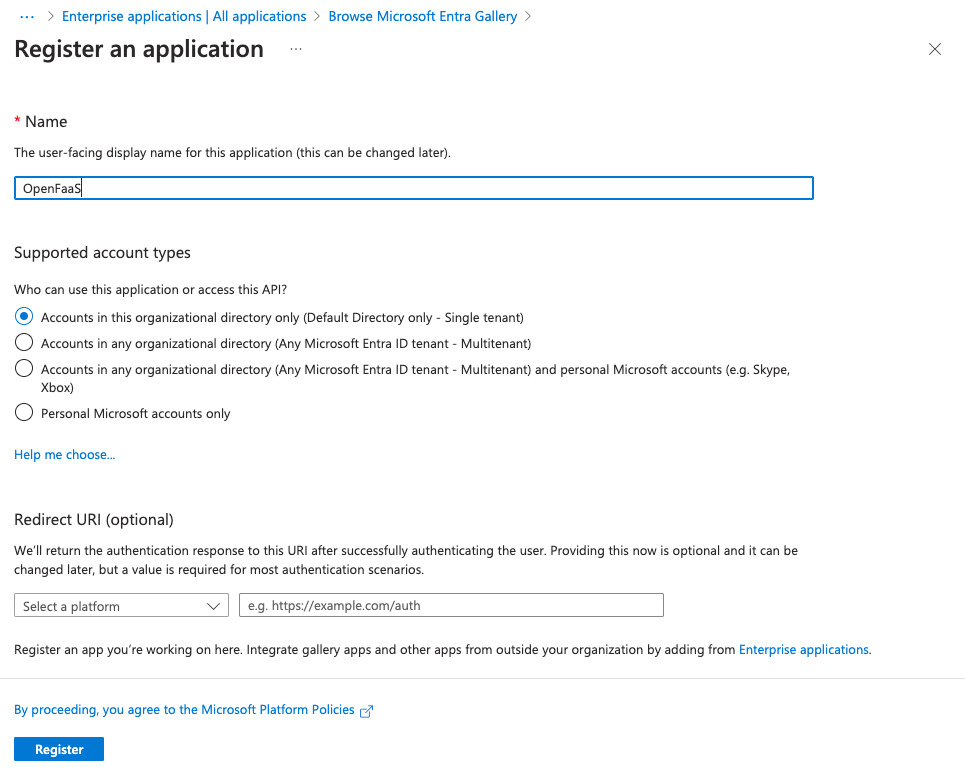
In the next form select the account types you would want to use. We will configure the redirect URI in the next step so this field can be left out for now. Click Register when done.
-
Configure allowed callback URL for the OpenFaaS dashboard and CLI.
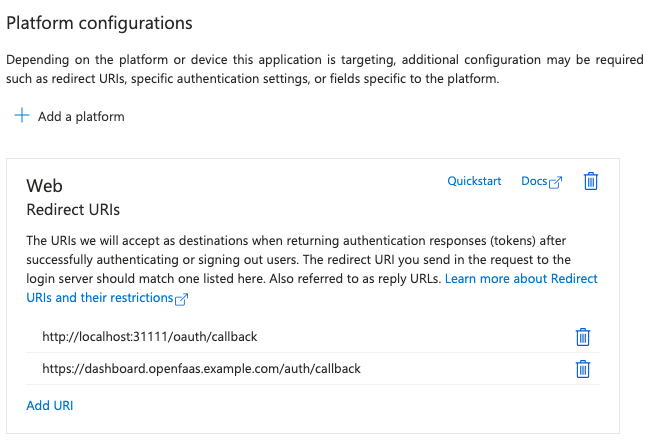
Browse to Identity -> Applications -> App registrations. In the All application tab select your OpenFaaS application. Next, under Authentication click Add platform and select Web.
Enter a redirect URI:
http://localhost:31111/oauth/callbackfor the CLI.- If you are deploying the OpenFaaS dashboard, you can add the redirect URI for your dashboard e.g
https://dashboard.openfaas.example.com/auth/callback.
You can add more URIs later once the first one has been registered.
-
Obtain client credentials
You will need to create a client secret for the OpenFaaS app. Navigate to Certificates and secrets for the OpenFaaS app registration and add a new client secret.
-
Register Microsoft Entra as a JwtIssuer with OpenFaaS
Create a JwtIssuer object in the
openfaasnamespace to register Microsoft Entra as a trusted issuer from OpenFaaS IAM.The
issfield needs to be set to the authority url of your app registration. The Authority url has the form:https://login.microsoftonline.com/{tenant}/v2.0.The
audfield contains a set of accepted audiences. For Microsoft Entra this is the application ID of your app registration.Both the Directory (tenant) ID and Application (client) ID can be found in the overview of your app registration in the Microsoft Entra admin center.
Example issuer for Entra:
apiVersion: iam.openfaas.com/v1 kind: JwtIssuer metadata: name: login.microsoftonline.com namespace: openfaas spec: iss: https://login.microsoftonline.com/1fe3798478-5987-2564-b4aa-99e587365024/v2.0 aud: - 068cb5cb-8cc3-4d57-8263-d6c6ce52ddff tokenExpiry: 12hThe
tokenExpiryfield can be used to set the expiry time of the OpenFaaS access token.